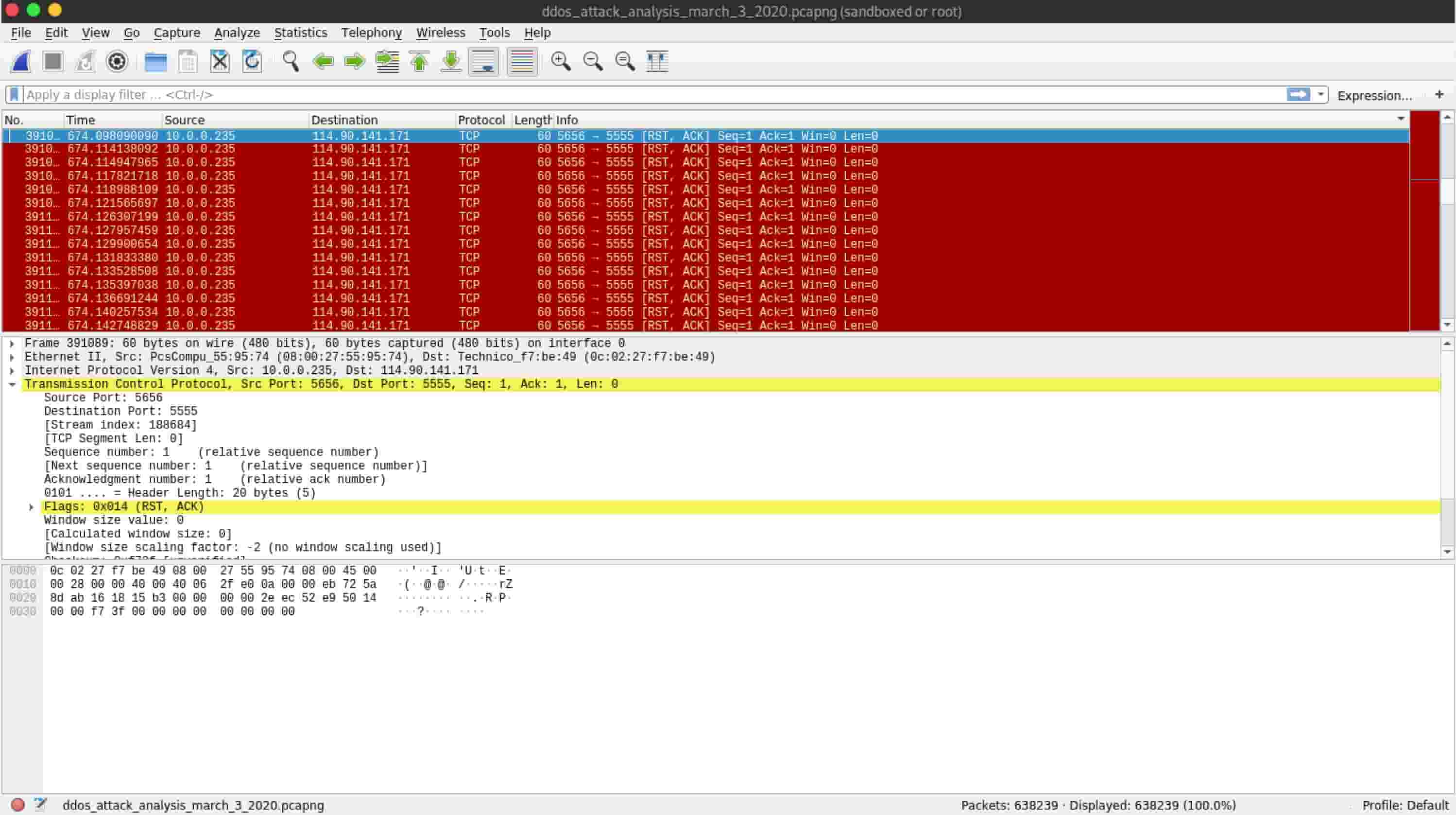
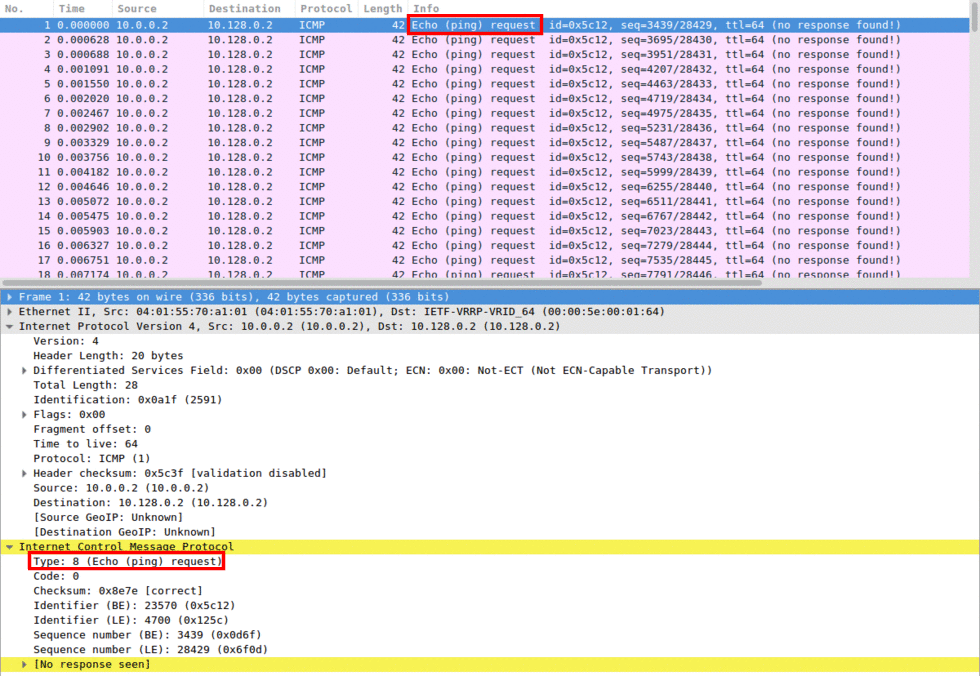
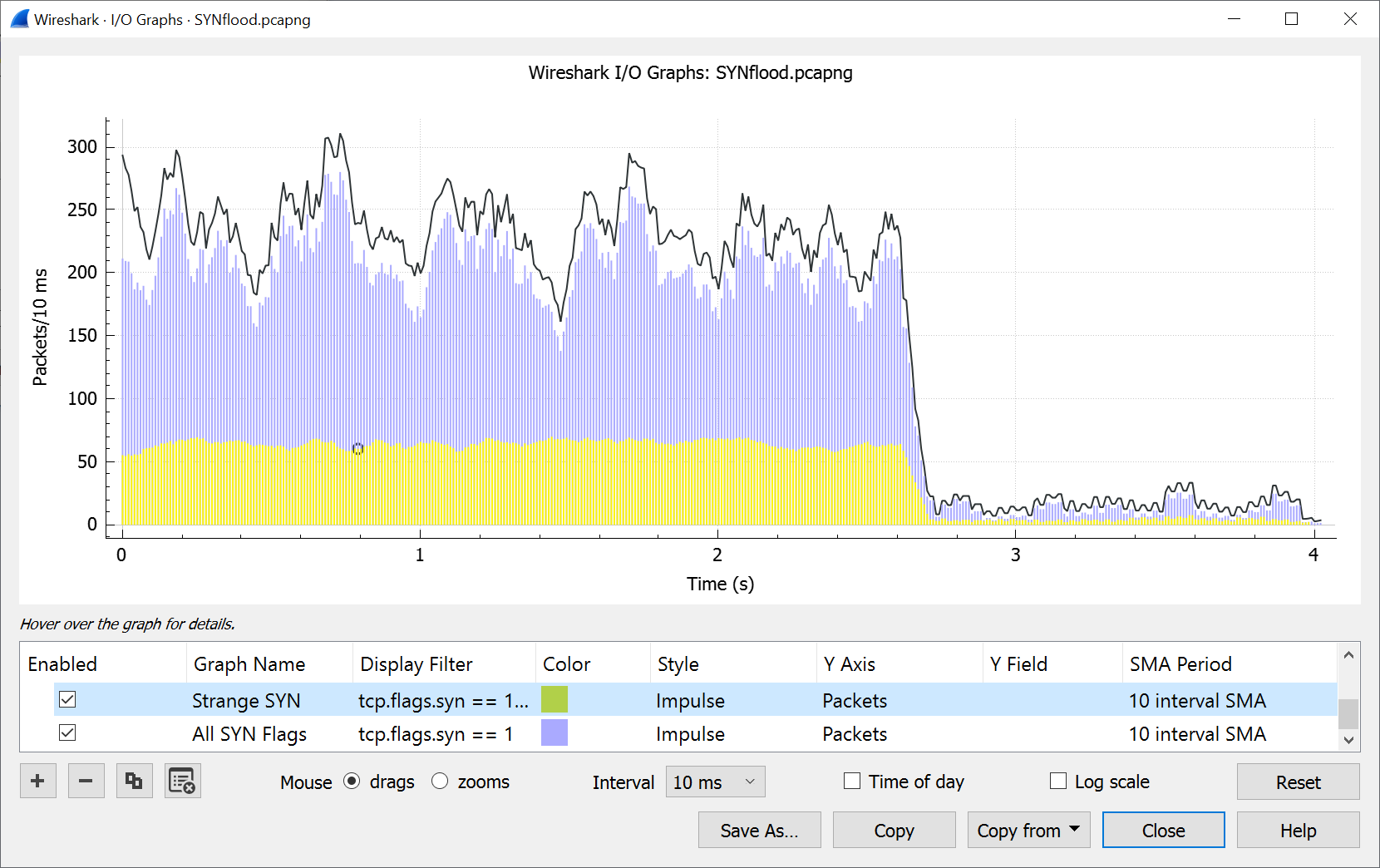
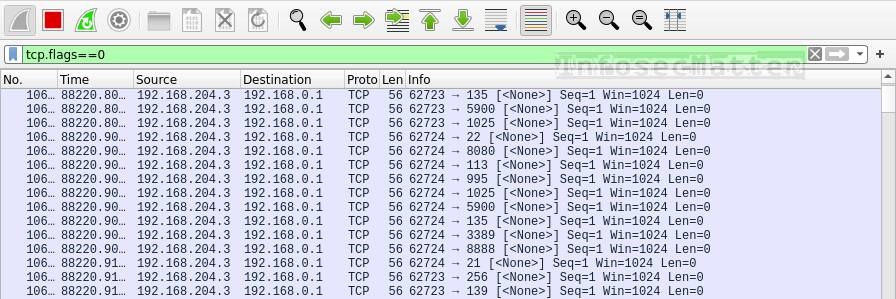
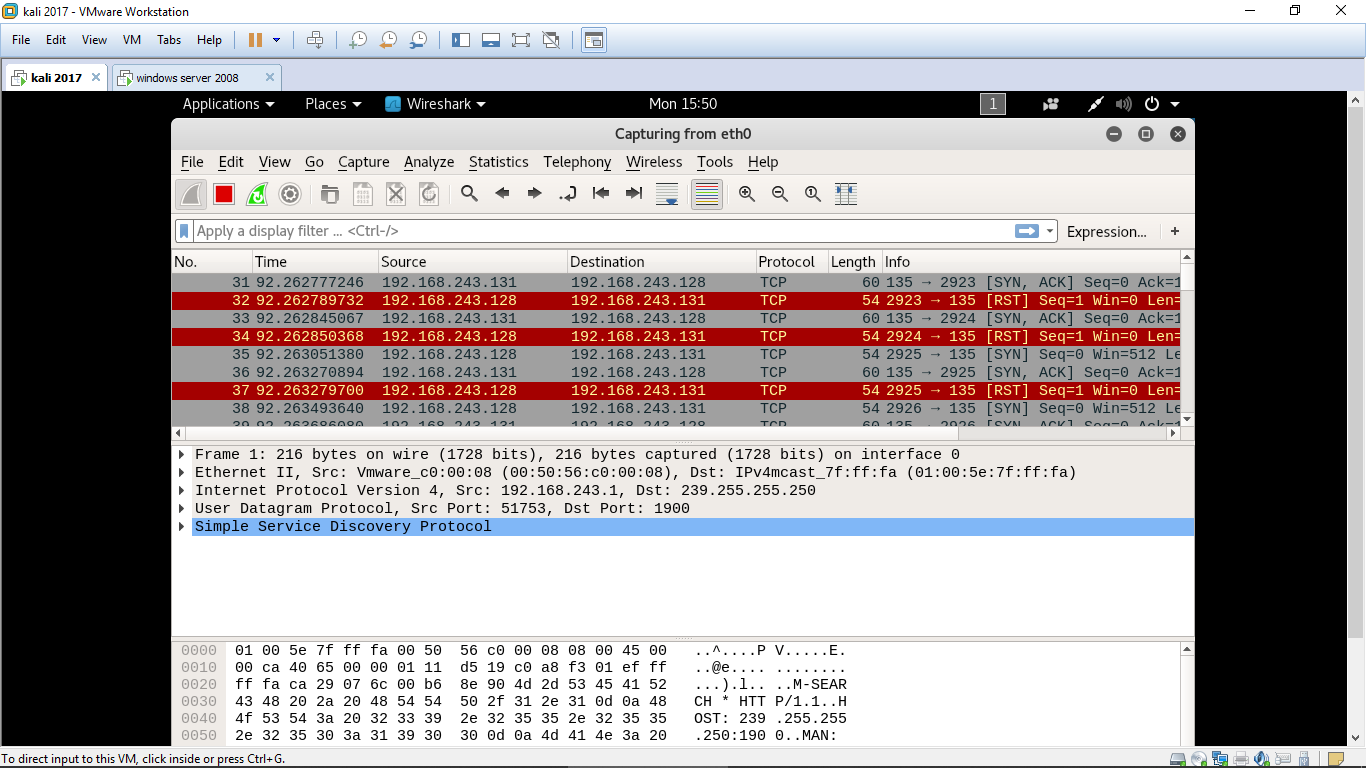
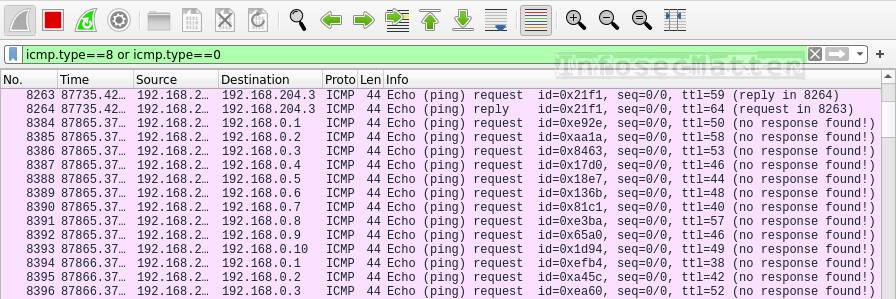
denial of service - How to identify a Ping of Death attack by analyzing its packet in Wireshark? - Information Security Stack Exchange

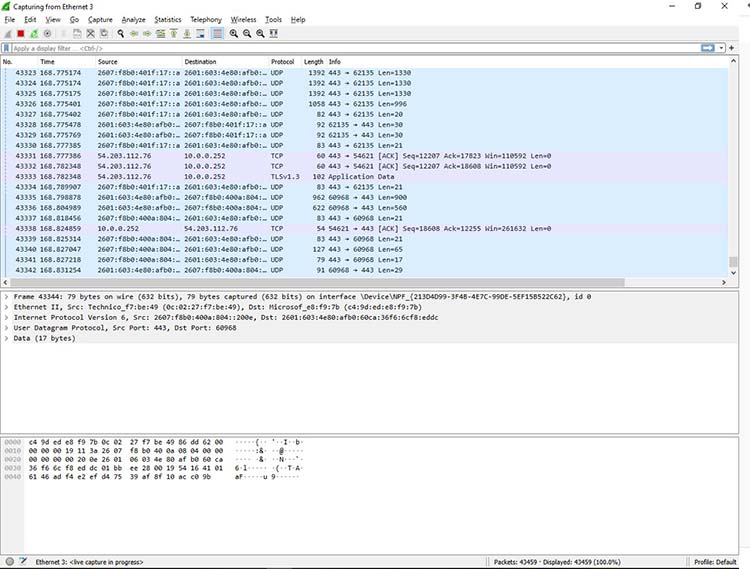
9.5.10 Analyze a DDo S Attack - 9.5 Analyze a DDoS Attack Use Wireshark to capture packets and - Studocu

Traffic analysis for incident response (IR): How to use Wireshark for traffic analysis | Infosec Resources
52. How To Detect Suspicious Traffic Using Wireshark - How To Detect DOS Attack By Wireshark - YouTube