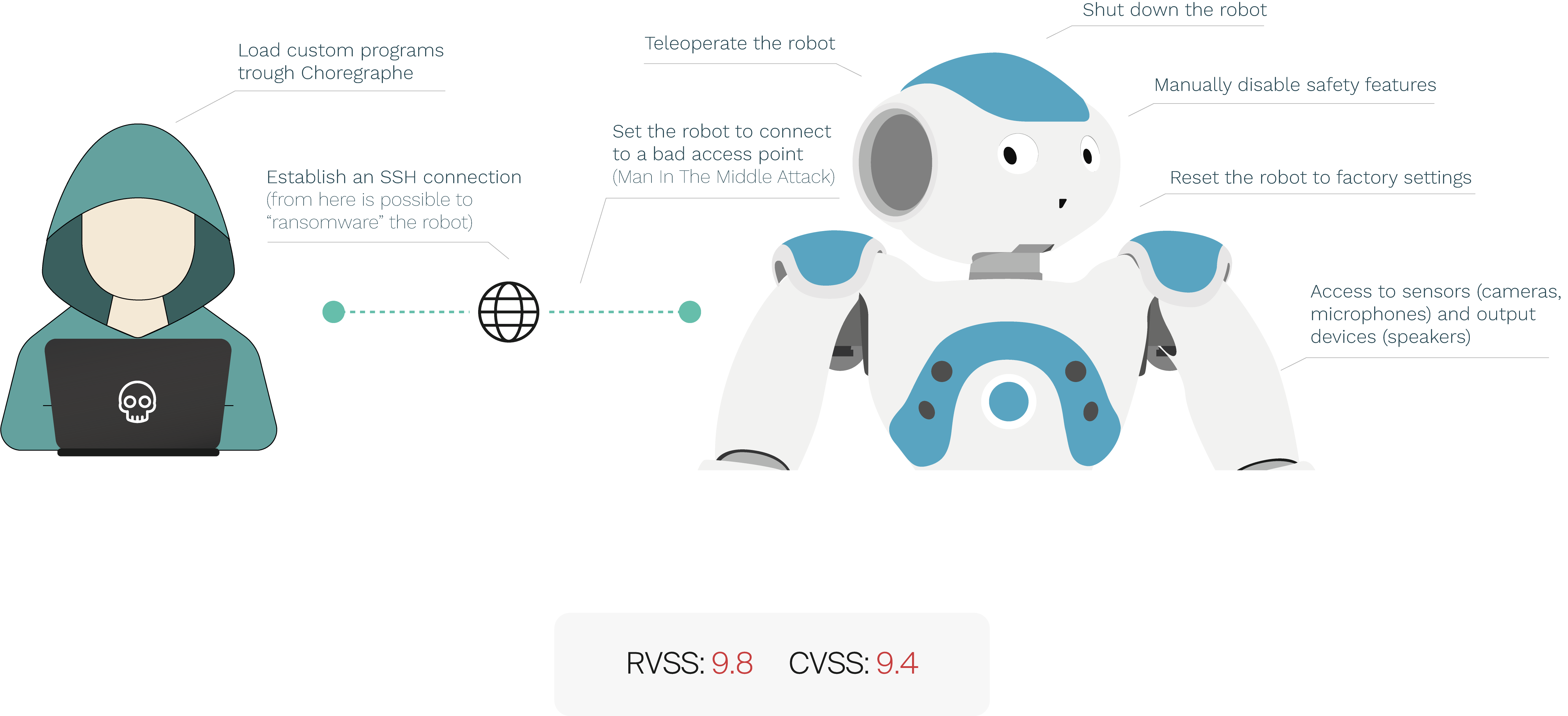
Towards an open standard for assessing the severity of robot security vulnerabilities, the Robot Vulnerability Scoring System (RVSS) | DeepAI

Could AI Chatbots Become a Security Risk? ChatGPT Demonstrates Ability to Find Vulnerabilities in Smart Contracts, Write Malicious Code - CPO Magazine